Understanding and Effectively Utilizing PowerShell Policies

Understanding and Effectively Utilizing PowerShell Policies
iPowerShell, by default, lets you run commands (cmdlets) via its console. To execute a script, you can create a notepad file with the script code, save it with a .ps1 file extension, and execute it via the PowerShell console. You can also directly paste the script onto the console for execution.
However, if it’s your first time executing a script via PowerShell, you’ll encounter the “running script is disabled” error. By default, script execution on PowerShell is disabled as a security measure to prevent malicious scripts from running on your system. Here we show you the two ways to enable the scrip execution policy on Windows PowerShell.
Disclaimer: This post includes affiliate links
If you click on a link and make a purchase, I may receive a commission at no extra cost to you.
How to Check Your Existing Execution Policy
You can use a PowerShell cmdlet to get your current execution policy. Knowing your current execution policy is necessary to know if you need a policy change or not.
To get your current execution policy for the current user:
- Open Windows PowerShell as administrator .
- Type the following command in the PowerShell console and hit Enter:
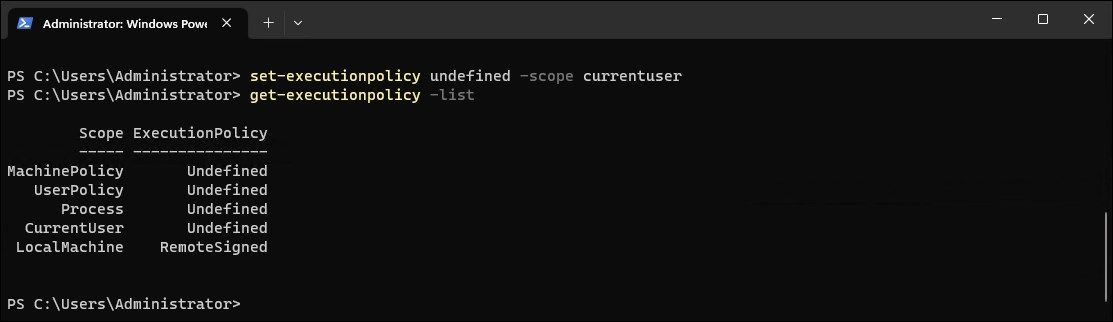
get-executionpolicy - Since you have encountered an error when executing the script, the return will likely showRestricted as your current execution policy.
- If you need to view the execution policy for all the supported scopes:
get-executionpolicy -list
You’ll need to change the execution policy to RemoteSigned to run local scripts without the error. You can change the execution policy from the Settings app and PowerShell.
How to Enable PowerShell Execution Policy Using the Settings App
You can change and set the PowerShell execution policy to RemoteSigned using the Settings app. All you have to do is tweak the PowerShell settings in the developers’ section to change the execution policy to enable PowerShell script execution.
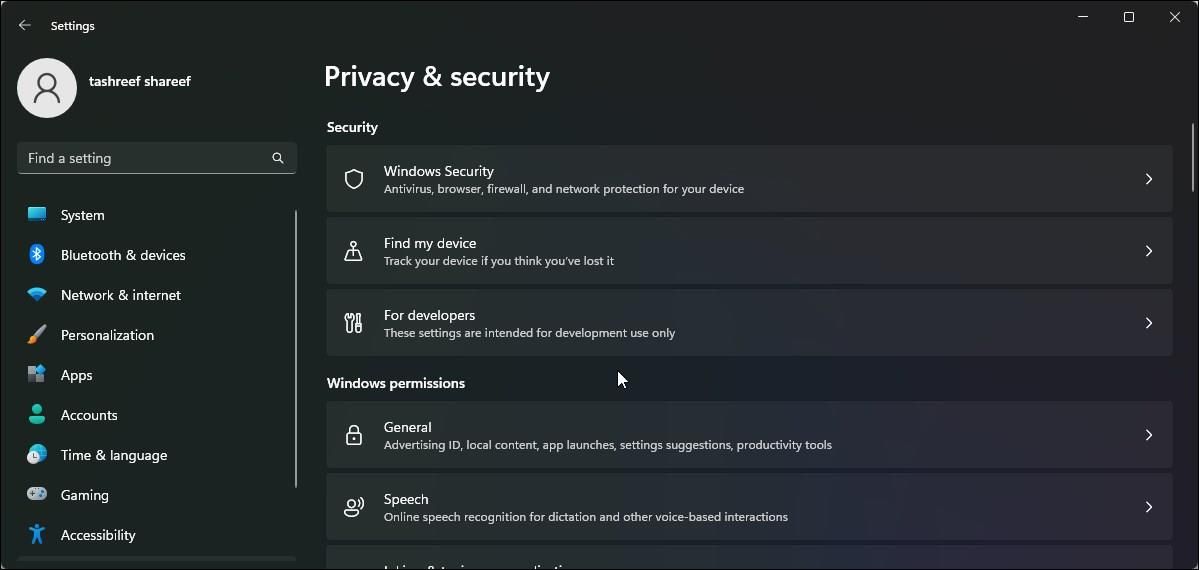
To change execution policy using Settings:
- PressWin + I to open Set tings.
- Open thePrivacy & Security tab in the left pane.
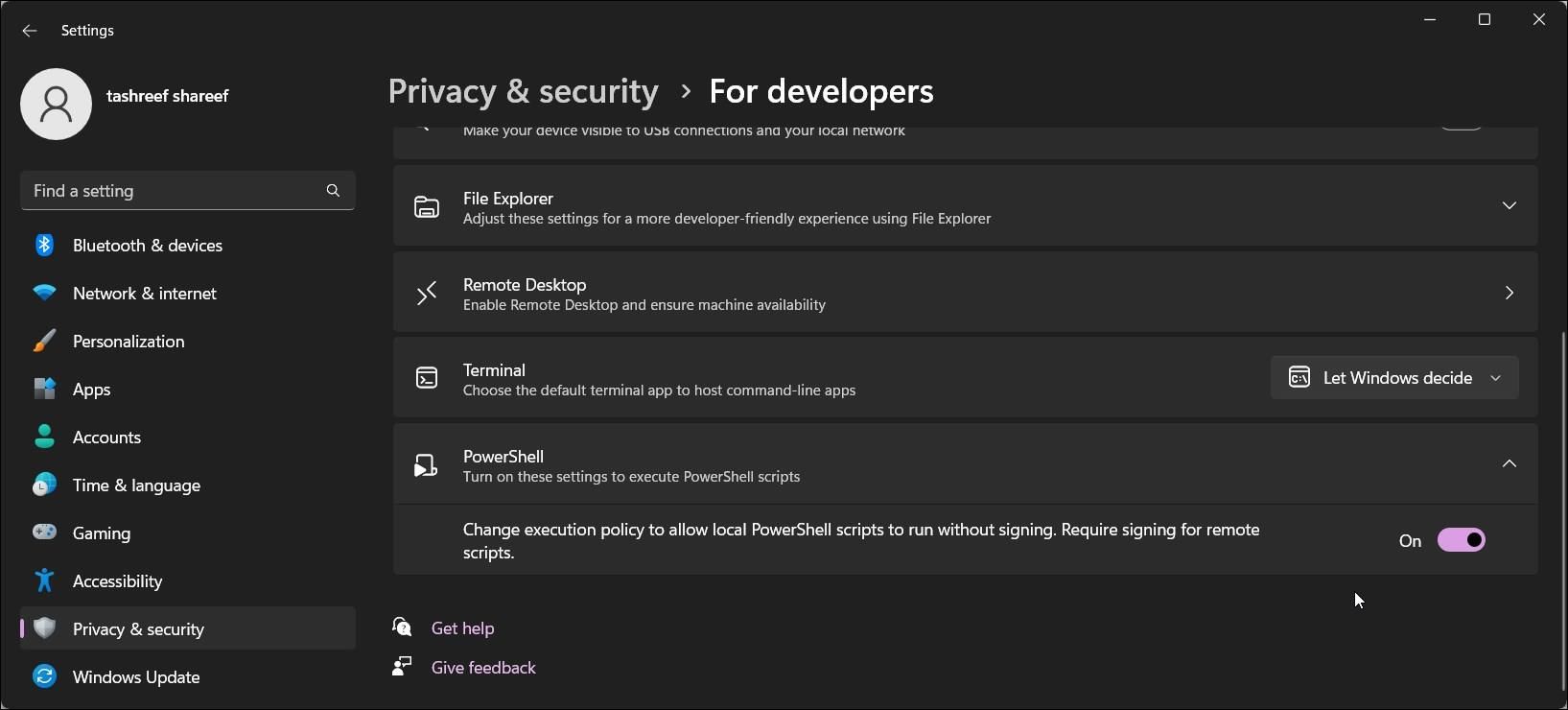
- Next, click onFor developers.

- Click to expand thePowerShell section.
- Toggle the switch to change the execution policy to allow local PowerShell scripts to run without signing - Require signing for remote scripts .

- Once done, open PowerShell, type getexecutionpolicy, and pressEnter . The execution policy for the current user is now set toRemoteSigned.
- If you need to disable the execution policy, toggle the PowerShell switch and set it toOff .
How to Allow Scripts to Run in PowerShell using PowerShell
You can use aPowerShell cmdlet to set the execution policy to RemoteSigned. The command-line interface makes it easy to change execution policy quickly without using the Settings app.
Also, the Settings app can only enable or disable the RemoteSigned execution policy. Whereas PowerShell lets you set other policies and scopes as well.
To change the execution policy using PowerShell:
- Open PowerShell as administrator .
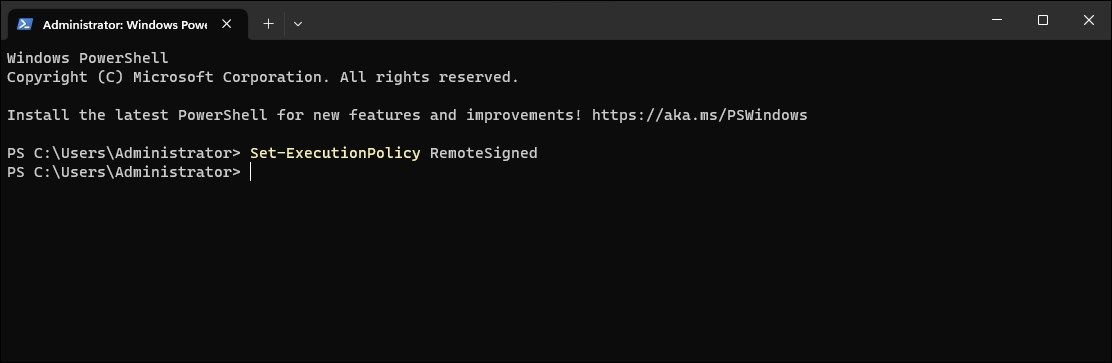
- In the PowerShell window, type the following command and pressEnter :
Set-ExecutionPolicy RemoteSigned - If prompted, pressA to confirm the action. This will set theRemoteSigned execution policy for all users. If you want to set the execution policy for theCurrent User only, use the Scope parameter followed by the username.
- For example, to set theRemoteSigned execution policy forCurrentUser , use the following command:
Set-ExecutionPolicy RemoteSgined -Scope CurrentUser - ReplaceCurrentUser in the above command with other users (Scope) as per your requirement.
How to Remove Script Execution Policy Using PowerShell
If you want to disable script execution, set the execution policy toUndefined using the Set_ExecutionPolicy cmdlet. This is a default state and prevents PowerShell from executing any scripts.
To disable script execution using PowerShell:
- Open PowerShell with elevated permission.
- Next, type the following command and press enter to disable script execution for all users:
Set-ExecutionPolicy undefined - The above command will set the execution policy default (undefined) for all the users. If you want to disable script execution for a specific scope, use the following command:
Set-ExecutionPolicy undefined -Scope CurrentUser - The above command will disable script execution forCurrentUser .
Understanding Execution Policies and Scopes
Simply put, PowerShell’s execution policy is a policy that controls how PowerShell executes config files and scripts. The intended purpose is to prevent users from accidentally running malicious scripts. The seven PowerShell execution policies are Default, Restricted, RemoteSigned, AllSigned, Unrestricted, Bypass, and Undefined .
The below table briefly explains all the PowerShell execution policies:
| Execution Policy | Enforcement |
|---|---|
| Default | Sets the default execution policy as Restricted on Windows Client and RemoteSigned on Windows Server. |
| AllSigned | Allows execution of publisher signed scripts. |
| Bypass | Unrestricted execution of scripts for larger applications. |
| RemoteSigned | Allows locally written script execution. Requires digital signatures for scripts downloaded from the internet. |
| Restricted | Doesn’t allow script execution, but only individual PowerShell commands. |
| Undefined | Sets execution policy to Restricted for Windows clients and RemoteSigned for Windows Server. |
| Unrestricted | Allow unsigned script execution with a warning for the scripts downloaded from the internet. |
Execution Policy Scope
You can set execution policy for a particular scope in PowerShell. The five execution policy scopes areMachinePolicy, UserPolicy, Process, CurrentUser, andLocalMachine .
The below table briefly explains all the execution policy scopes:
| Execution Policy Scope | Enforcement |
|---|---|
| UserPolicy | Configured by a Group Policy for the current user. |
| Machine Policy | Configured by a Group Policy for all the users. |
| CurrenUser | Configured for the current user and stored in HKEY_CURRENT_MACHINE registry subkey. |
| LocalMachine | Configured for all users and stored in HKEY_CURRENT_MACHINE registry subkey. |
| Process | Affects current PowerShell session and automatically deleted when the session is closed. |
Add or Remove PowerShell Script Execution Policy on Windows
Script execution on PowerShell is disabled by default for Windows clients and set to RemoteSigned for Windows server. Power users, however, can change execution policies to run local, signed, and unsigned PowerShell scripts.
Alternatively, you can bypass the PowerShell execution policy by pasting the script into a PowerShell console or ECHO your script into PowerShell standard input. This is useful if you want to execute scripts without changing the execution policy.
Also read:
- [New] In 2024, Unlock Creative Potential with KineMaster Skills + 10 Superior Alternatives
- [New] The Updated Review Sony's Blu-Ray and HD Masterpiece
- [New] Youtube Ascension From a Niche Channel to Million-Sub Haven
- Addressing Unsuccessful Image Saving on Win11 PC
- Clarifying Computer Storage: C, D Distinctions
- Essential Steps for Preventing Heat in W11 Systems
- Mastery of AMD Graphics Driver Updates in the Windows Ecosystem
- Simple Solutions: Resolving Silent Streams on Netflix
- Stellar Repairs Not Uniformly Applied to All Videos.
- Unlock New Dimensions Exploring Xbox One's Zooming Feature for 2024
- Title: Understanding and Effectively Utilizing PowerShell Policies
- Author: David
- Created at : 2024-10-27 21:07:55
- Updated at : 2024-11-01 19:06:32
- Link: https://win11.techidaily.com/understanding-and-effectively-utilizing-powershell-policies/
- License: This work is licensed under CC BY-NC-SA 4.0.