Modifying Account Access Restrictions Post-Failed Logon

Modifying Account Access Restrictions Post-Failed Logon
Windows has a policy setting that can lock someone out from signing in if they enter the wrong local account password too many times. The user is not allowed to sign in for a set number of minutes after being locked out, but you can change this lockout duration.
Here’s how to change how long someone using a specific Windows machine is locked out if they enter the wrong login credentials a certain number of times. You must be signed in as an administrator to change this policy.
Disclaimer: This post includes affiliate links
If you click on a link and make a purchase, I may receive a commission at no extra cost to you.
How to Change the Duration a User Is Locked Out of Their Account via Local Security Policy
This method will work as long as the system is running the Pro, Enterprise, or Education edition of Windows 10 or 11.
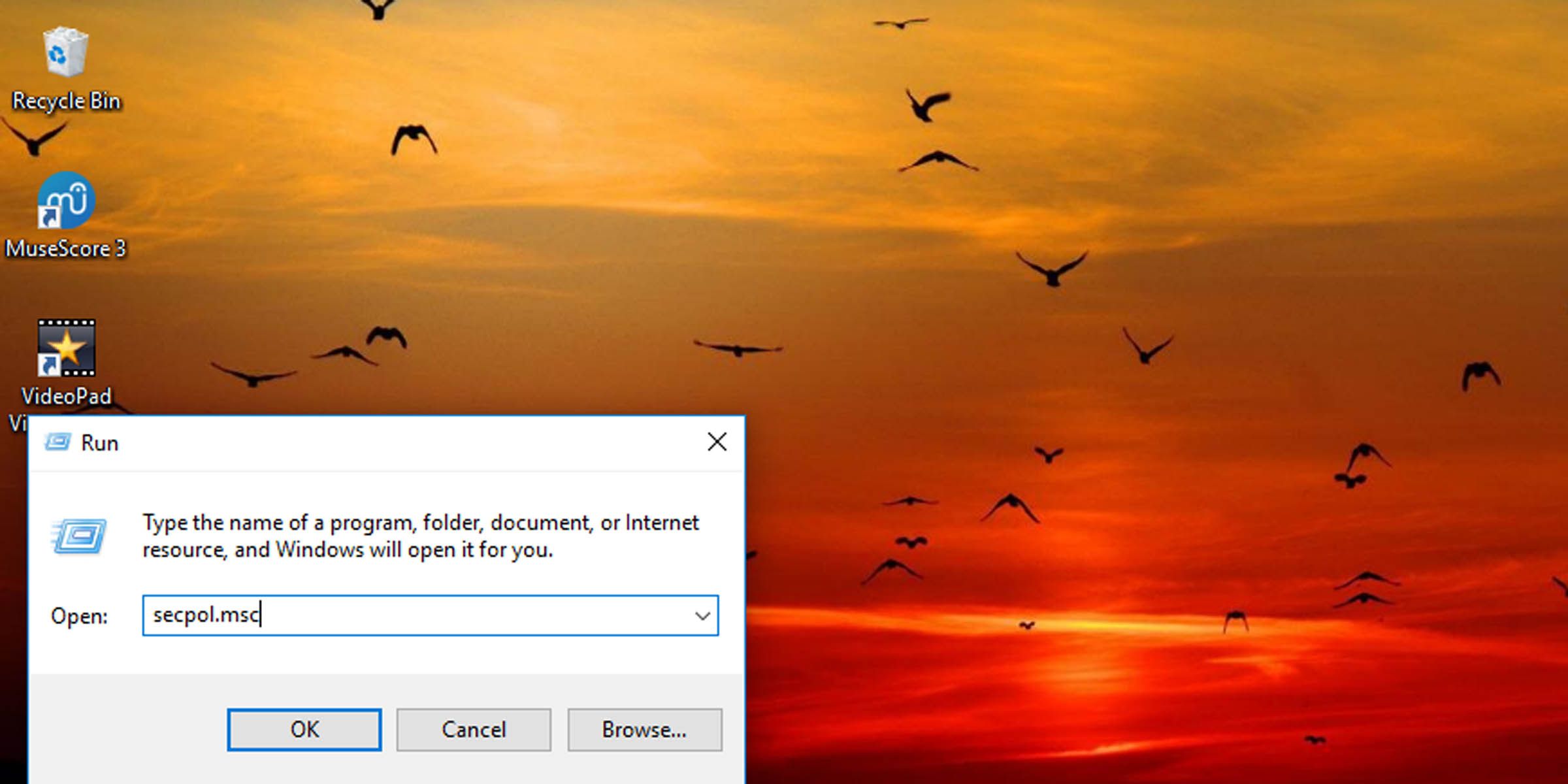
- Press Windows key + R to open the Run dialogue.
- Type “secpol.msc” into the text field and hit Enter.

- On the left pane, click on the Account Lockout Policy folder under Account Policies.
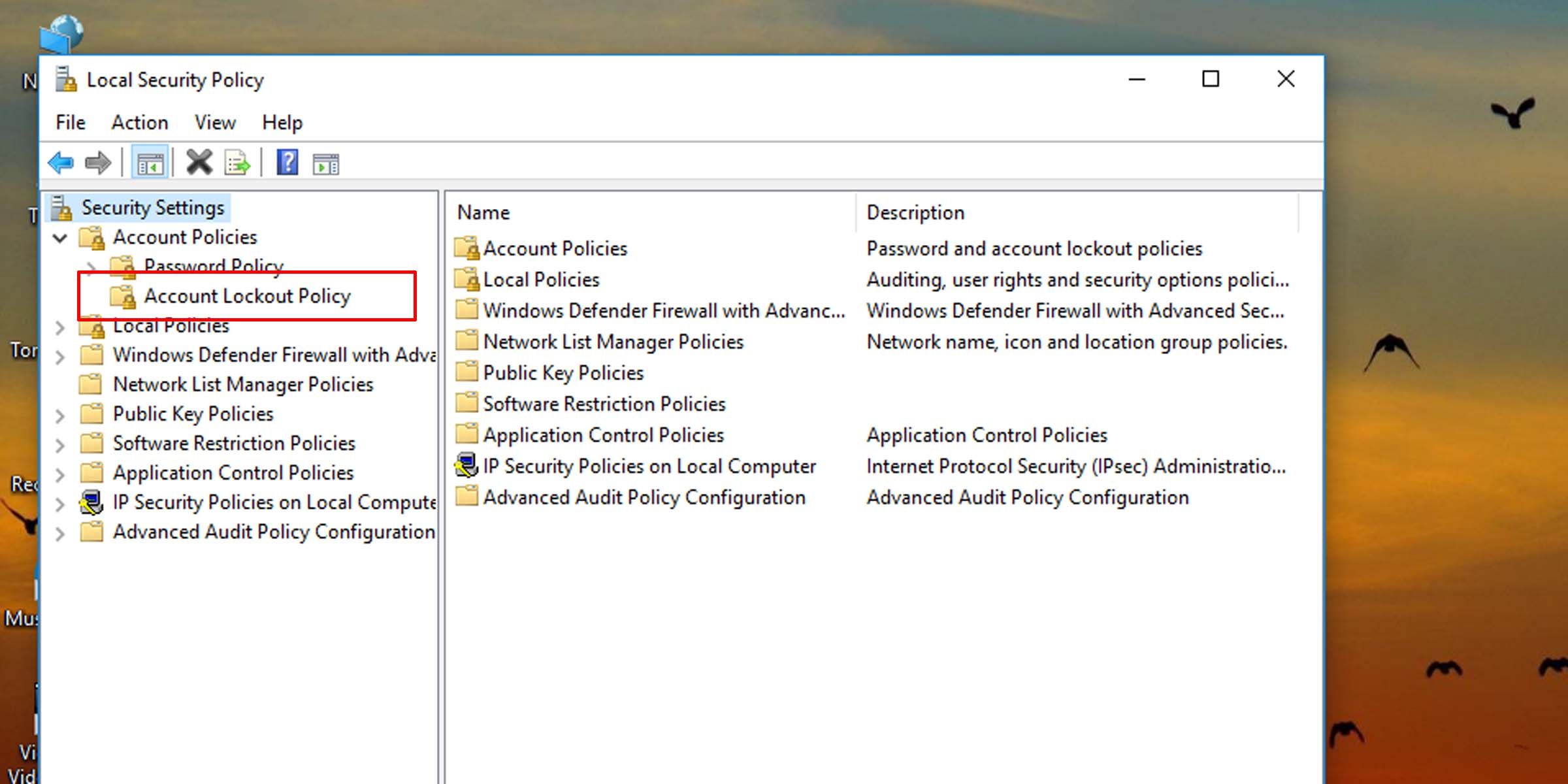
4. On the right pane, double-click on Account lockout duration.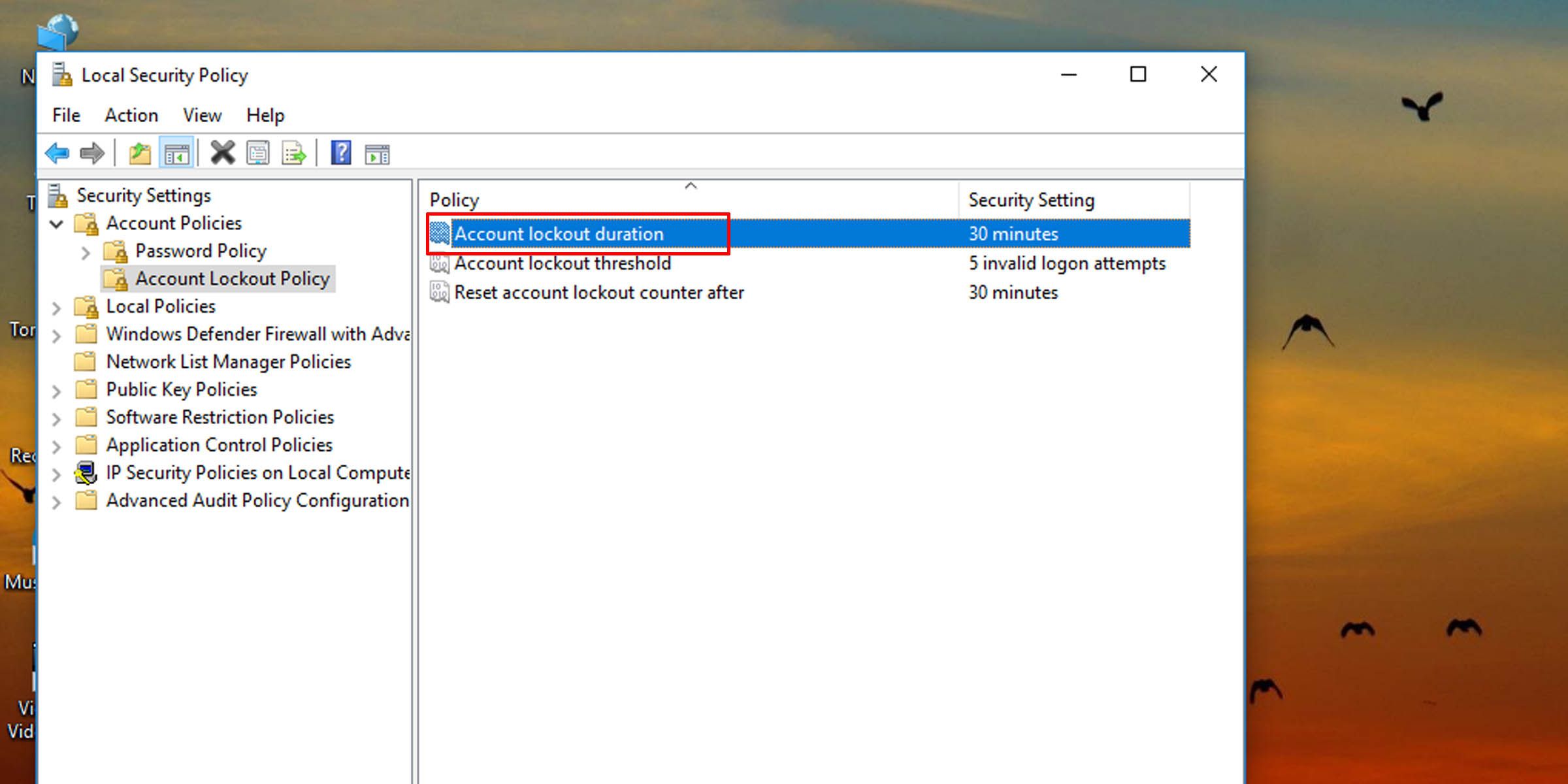
5. Type in a number between zero and 99,999, and hit OK. This will set how long (in minutes) the system will need before it accepts another login attempt.
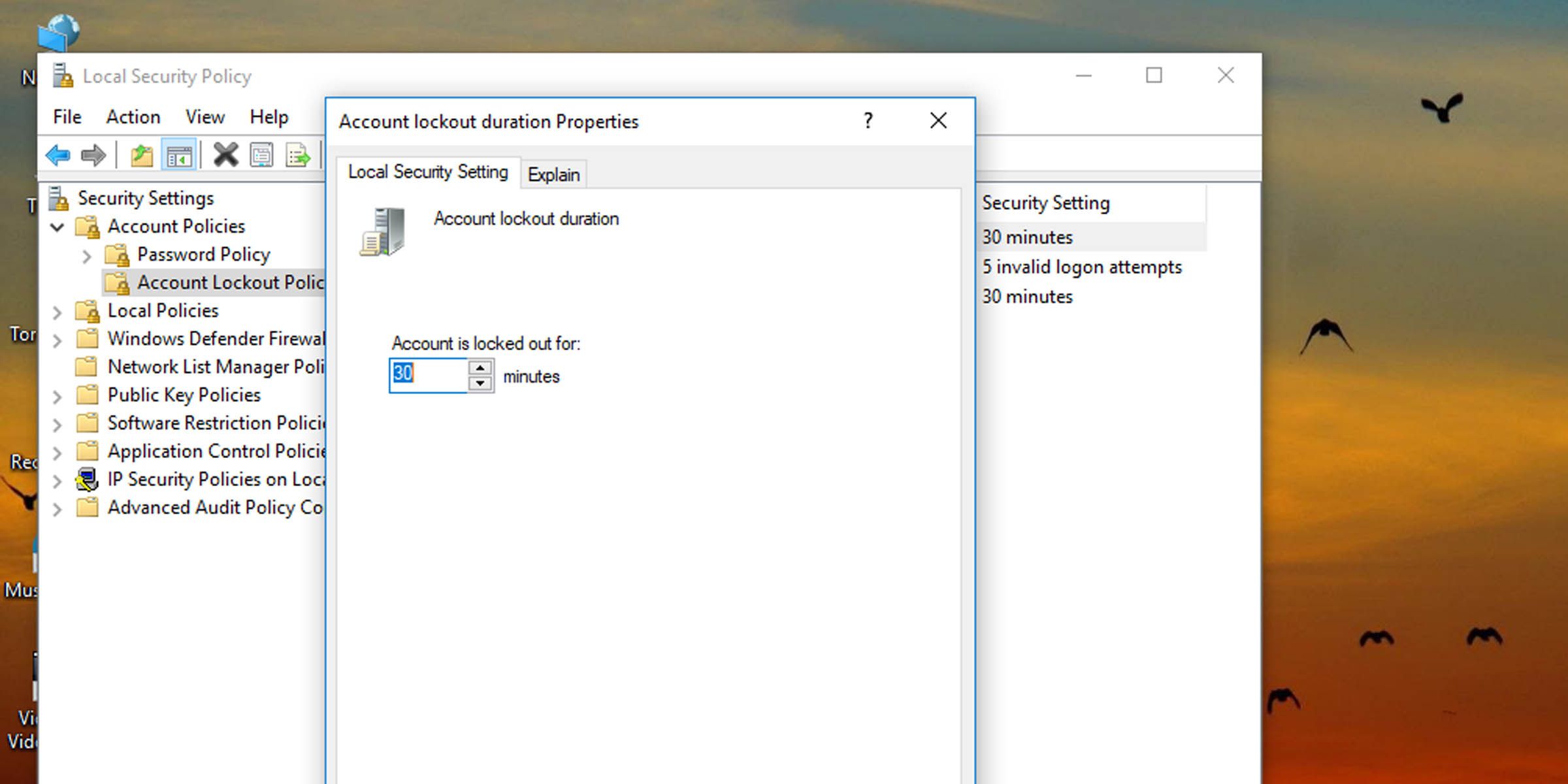
How to Change the Account Lockout Duration in Windows via the Command Prompt
If the system isn’t running the Pro, Enterprise, or Education edition of Windows 10 or 11, you’ll need to use the command prompt to change how long a user must wait before signing in again after failed login attempts.
- Open Command Prompt as Administrator . You can also perform this task with Windows PowerShell if you prefer.
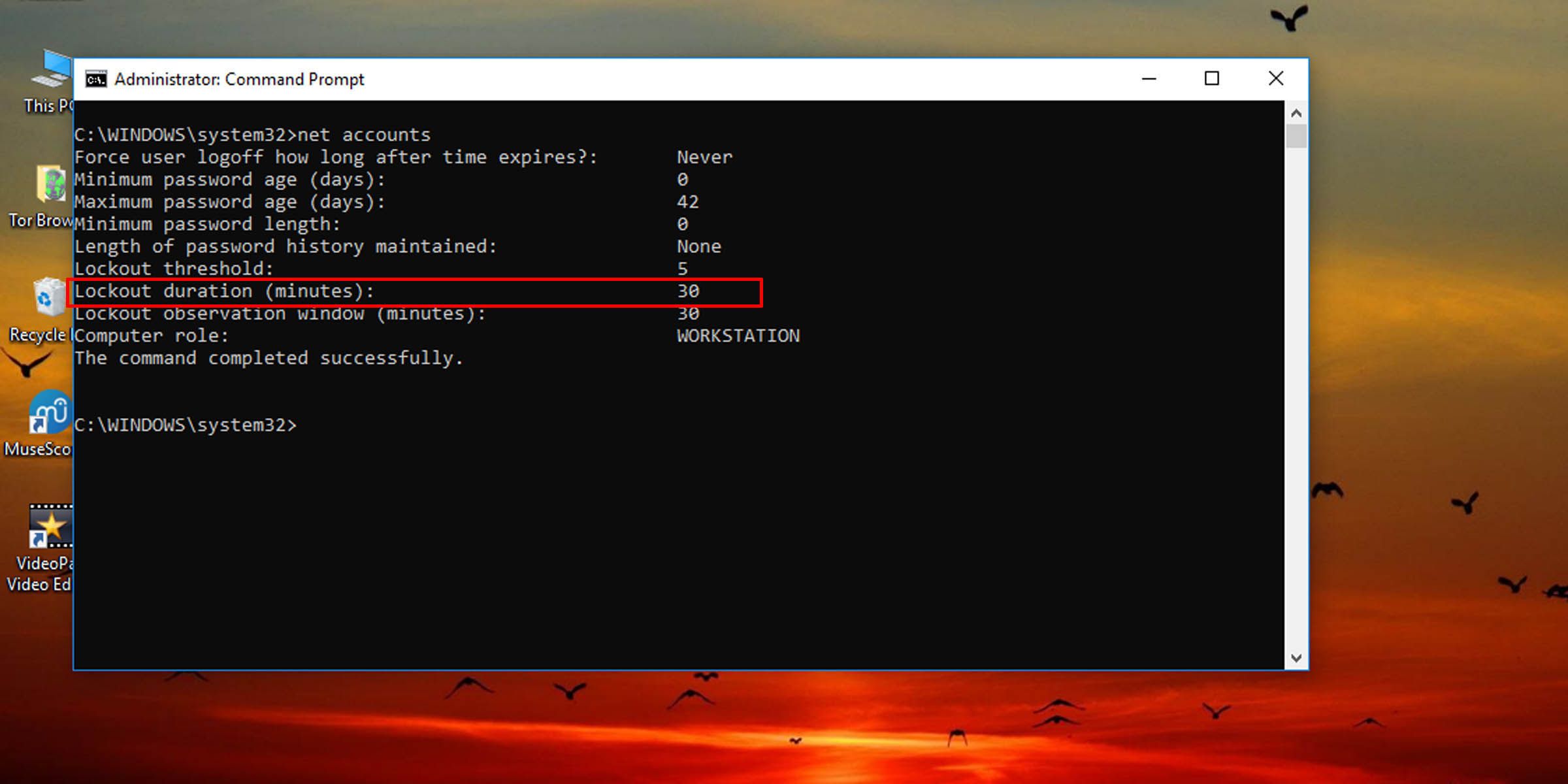
- Type the following command into the console and hit Enter:
net accounts
- This will pull up information, among other things, about how long this account lockout duration is currently set.
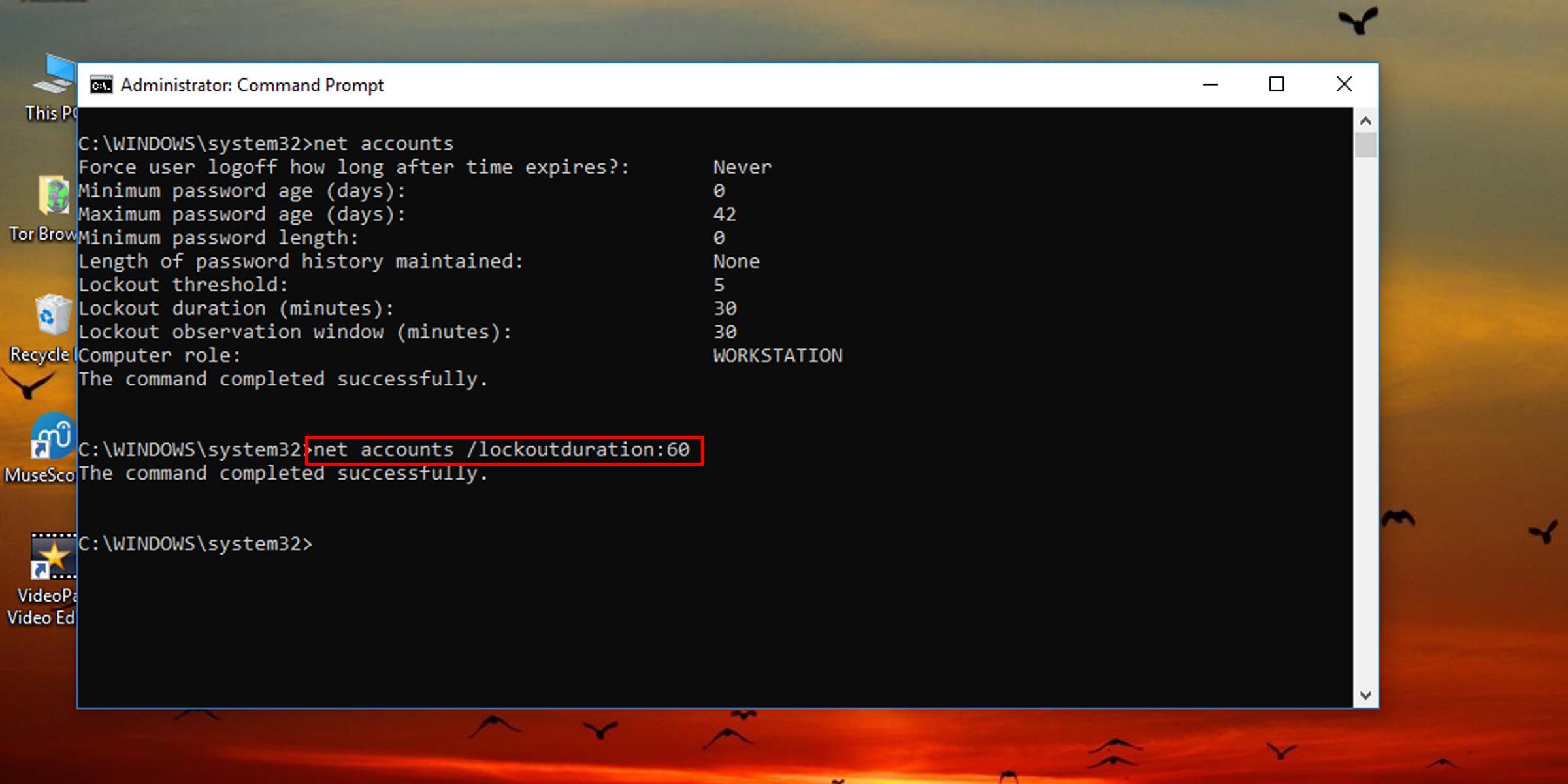
- To change account lockout duration on Windows 10 and 11, type the following command into the console and hit Enter. Replace the number “60” in the command with any other number from zero to 99,999 to set how many minutes a user will have to wait before being allowed to try and log in again.
net accounts /lockoutduration:60
Setting this value to zero means the locked-out user will not be able to sign in unless an administrator intervenes and unlocks it. Also, the account lock-out duration must be greater than or equal to the time for the system to automatically reset the number of failed login attempts .
If you don’t ever want users to be locked out of their local accounts, you must change the number of failed login attempts a user is allowed.
Find the Balance Between Security and Convenience
Setting account lockout duration too high will cause inconvenience, but if you set it to zero, an administrator will have to be contacted each time a user locks themselves out. Find a balance between security and convenience when it comes to changing how long a user is locked out after a set number of failed login attempts.
Here’s how to change how long someone using a specific Windows machine is locked out if they enter the wrong login credentials a certain number of times. You must be signed in as an administrator to change this policy.
Also read:
- [New] Easy Process How to Save Twitter Videos on an Android Device for 2024
- [New] In 2024, Revamping Online Speech Chromebook's Top 5 Voice Alteration Tools Revealed
- [Updated] 2024 Approved Directing Content Flow Uploading IMovie Films to YouTube
- Fixing Windows 11/10 NVIDIA CP Error with Ease
- How to Enable Support for Emoji 15 on Windows 11
- In 2024, How to Track WhatsApp Messages on Oppo Reno 11F 5G Without Them Knowing? | Dr.fone
- In 2024, Instagram's Best Grids Built by the Top Tools Compiled Here
- Insight Into Windows AggregatorHost.exe: Purpose, Usefulness, and Safety
- Installing VirtualBox on Windows? Set Up the Dependencies First for Error-Free Installation
- Methodology to Rectify Managed Chromium & Microsoft Edge Configurations
- Navigating Soundtrack Selection in Unboxing Filmmaking
- Switch to Shadows: Making Paint Dark
- Top 4 Android System Repair Software for Infinix Note 30 Pro Bricked Devices | Dr.fone
- Top 8 Windows Timer Apps: Perfecting Pomodoros
- Video File Repair - How to Fix Corrupted video files of HTC U23 Pro on Windows?
- Title: Modifying Account Access Restrictions Post-Failed Logon
- Author: David
- Created at : 2024-10-15 16:45:33
- Updated at : 2024-10-21 05:06:45
- Link: https://win11.techidaily.com/modifying-account-access-restrictions-post-failed-logon/
- License: This work is licensed under CC BY-NC-SA 4.0.