Keep an Eye on Your Window's Gatekeeping Credentials Trend

Keep an Eye on Your Window’s Gatekeeping Credentials Trend
Windows lets you create multiple user accounts to let multiple users use a single computer. But what if you suspect someone to have accessed your PC or user account without your knowledge?
While physically monitoring your computer all the time is not feasible for most people, the built-in Windows log utility, Event Viewer, can reveal the recent activities on your computer, including login attempts. Here we show you how to audit failed and successful login attempts in Windows using Event Viewer and other methods.
Disclaimer: This post includes affiliate links
If you click on a link and make a purchase, I may receive a commission at no extra cost to you.
How to Enable Logon Auditing via Group Policy Editor
You need to enable logon auditing in Group Policy Editor to be able to view login audit in Event Viewer. While this feature may be enabled by default on some computers, you can also enable logon auditing manually by following these steps.
Note that Group Policy Editor is only available on the Pro, Edu, and Enterprise edition of the Windows OS. If you are on the Home edition, follow our guide toenable gpedit in the Windows home edition .
Note that if you don’t configure your Group Policy for Logon Auditing, you can only view the successful login attempts in Event Viewer.
Once you have the Group Policy Editor enabled, follow these steps to enable logon auditing:
- PressWin + R to openRun .
- Typegpedit.msc and clickOK to open theGroup Policy Editor.
- Next, navigate to the following location:
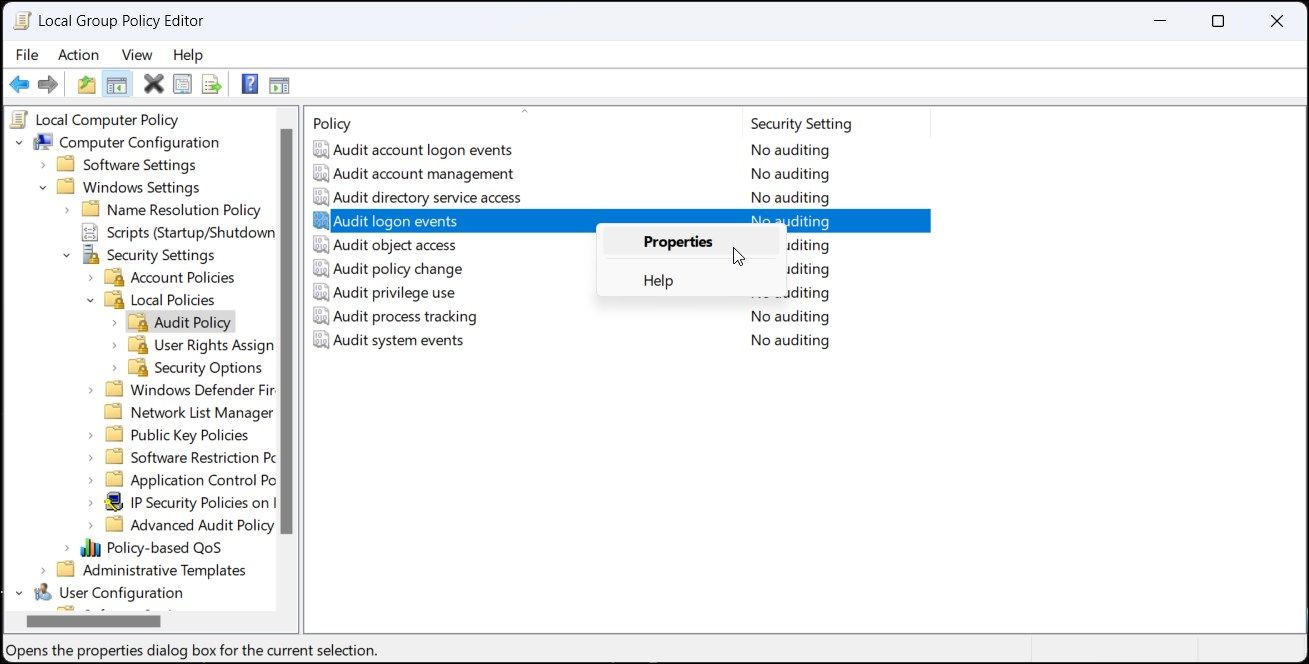
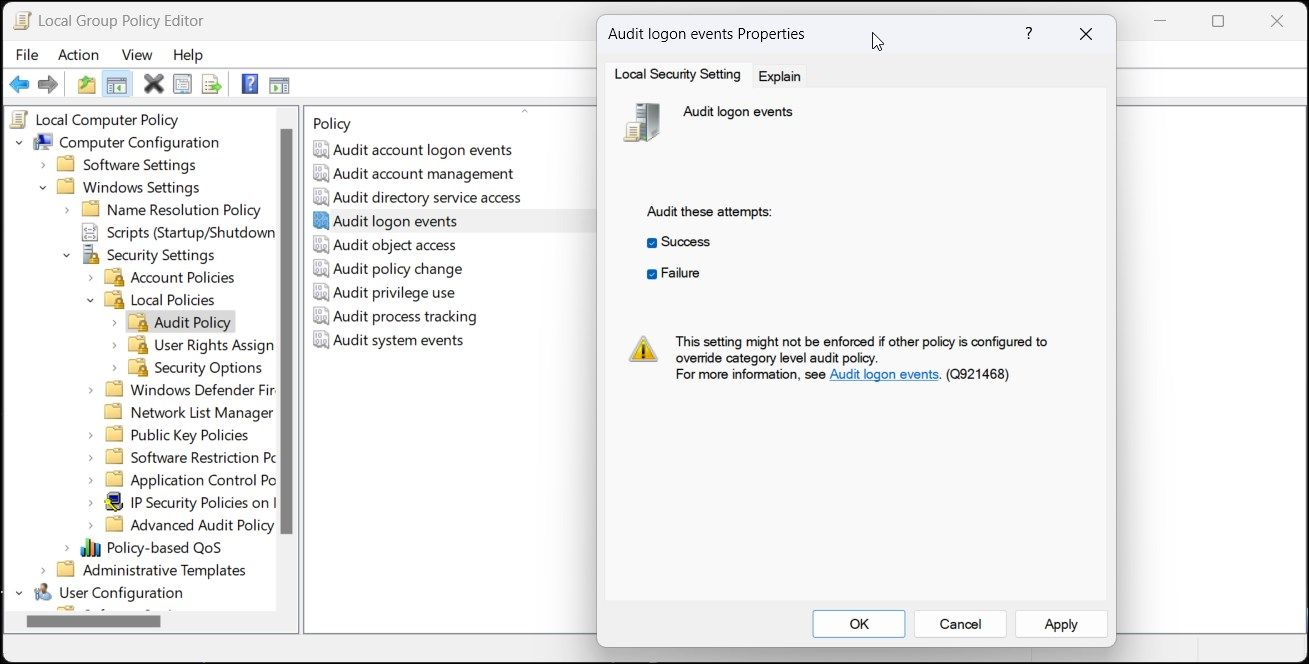
Computer Configuration > Windows Settings > Security Settings > Local Policies > Audit Policy - In the right pane, right-click onAudit logon events and selectProperties .

- In theProperties dialog, selectSuccess andFailure options under theAudit these attempts section.

- ClickApply andOK to save the changes.
Close Group Policy Editor and move to the next set of steps to view login attempts in Event Viewer.
How to View Failed and Successful Login Attempts in Event Viewer
TheEvent Viewer lets you view Windows logs for the application, security, system, and other events. While a useful application to troubleshoot system issues, you can use it to audit login events on your Windows PC.
Follow these steps to view failed and successful login attempts in Windows:
- Press theWin key and typeevent viewer. Alternatively, click onSearch in the taskbar and typeevent viewer.
- Click onEvent Viewer from the search result to open it.
- In the left pane, expand theWindows Logs section.

- Next, selectSecurity .
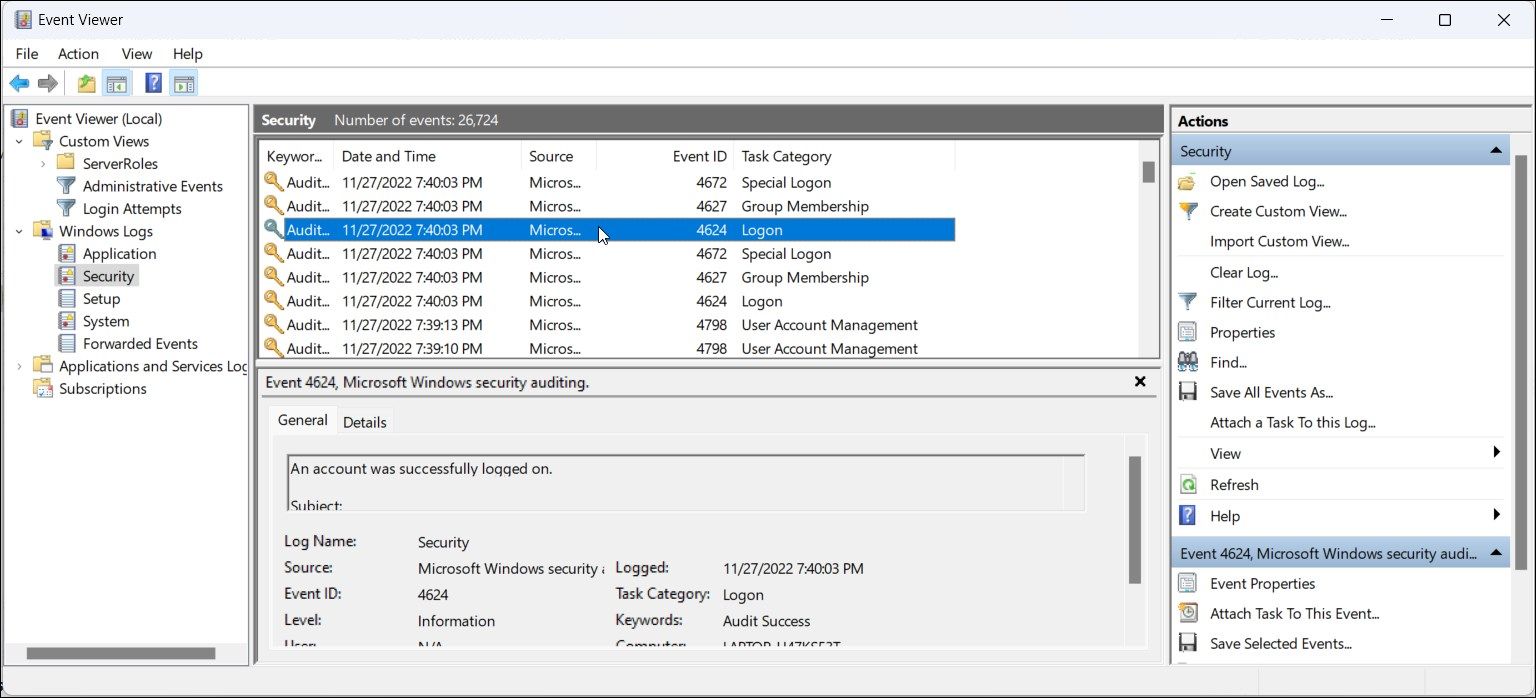
- In the right pane, locate theEvent 4624 entry. It is a user logon event ID, and you may find multiple instances of this ID in the event log.
- To find failed login attempts, locateEvent ID 2625 entries instead.
- Next, select theEvent 4624 entry you want to view, and Event Viewer will display all the related information in the bottom section. Alternatively, right-click on the event entry and selectProperties to view detailed information in a new window.
How to Decipher the Logon Entries in Event Viewer
While Event ID 4624 is associated with logon events, you will likely find multiple instances of this entry occurring every few minutes in the log. This is due to Event Viewer recording every logon event (whether from the local user account or system services such as Windows Security) with the same event ID**(Event 4624**).
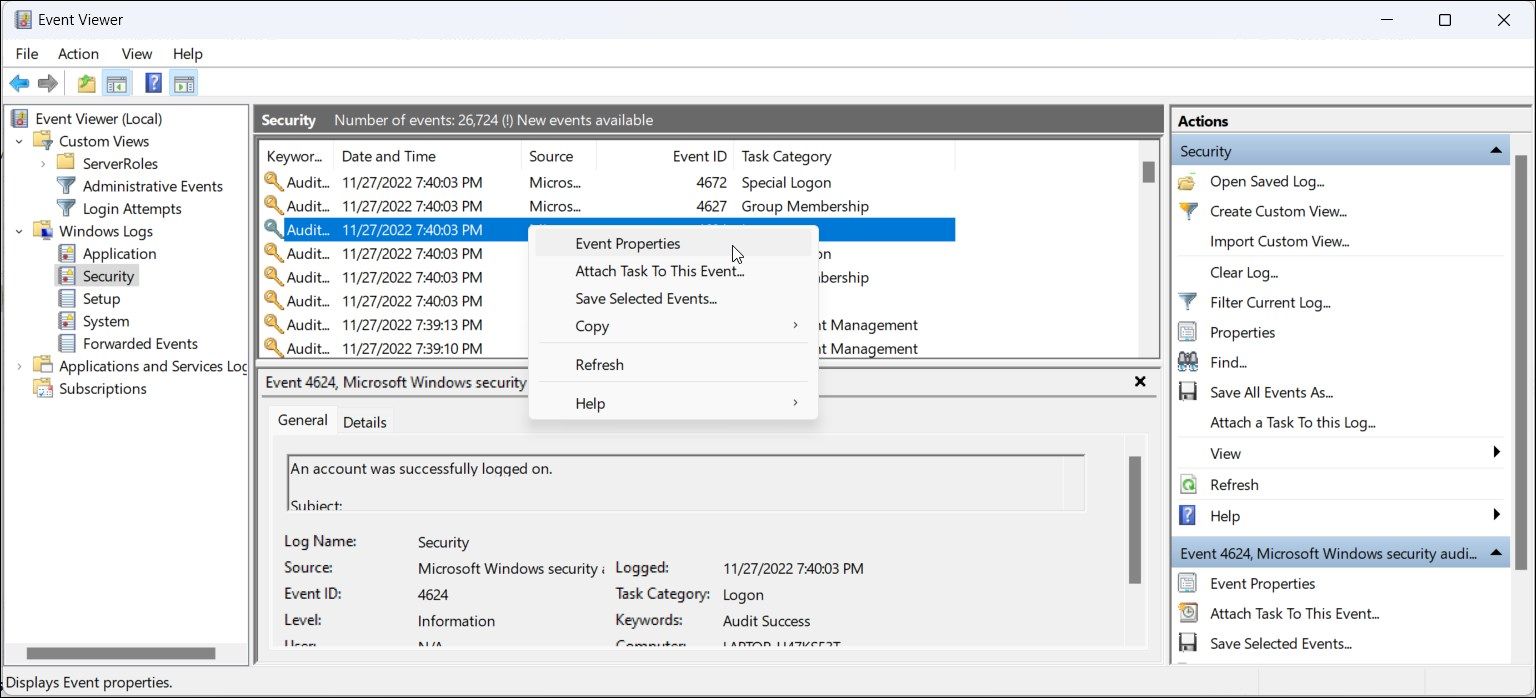
To identify the source of login, right-click on the event record and selectProperties . In theGeneral tab, scroll down and locate theLogon information section. Here, theLogon Type field indicates the kind of logon that occurred.
For example,Logon Type 5 indicates a service-based login, whileLogon Type 2 indicates user-based login. Know more about the different logon types in the table below.
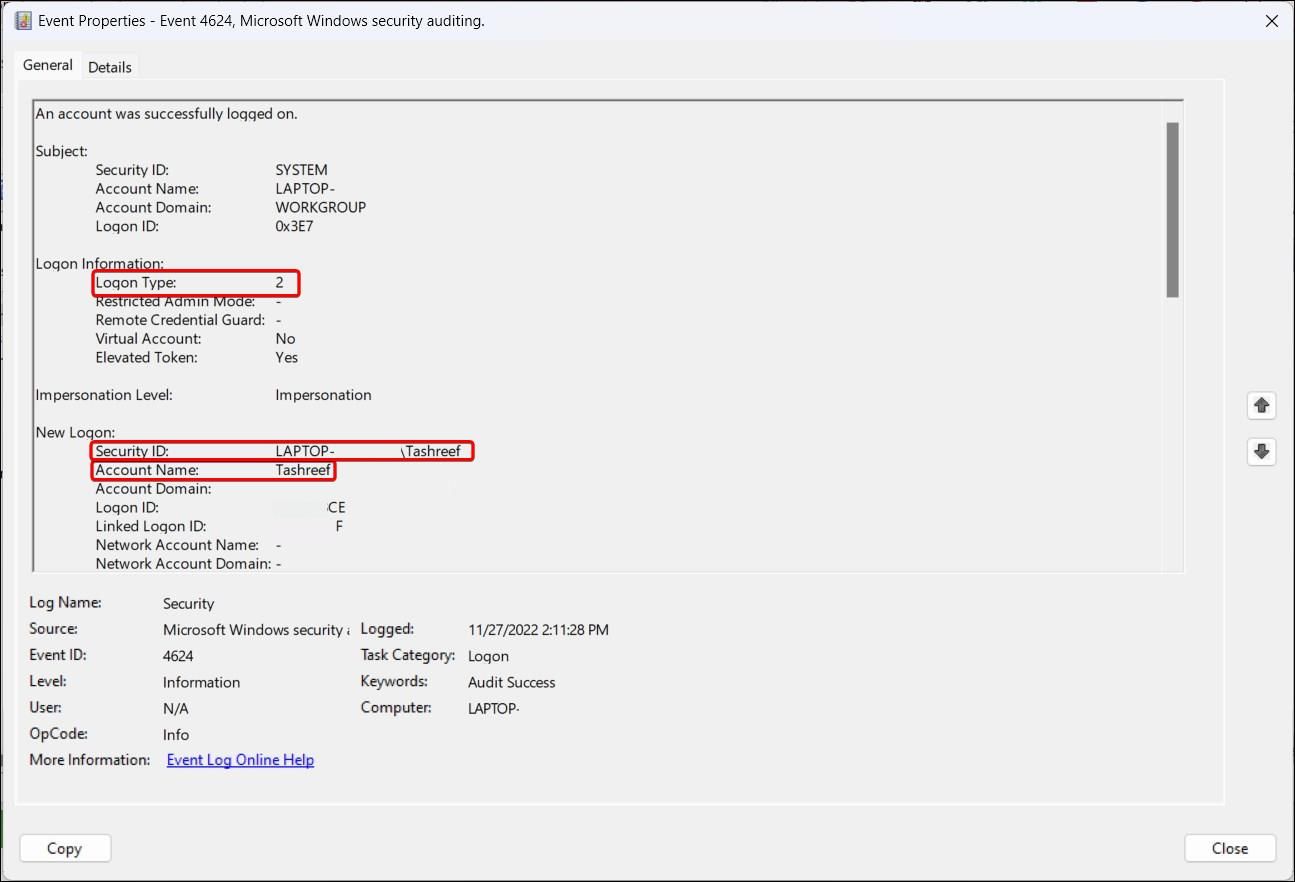
Next, scroll down to theNew Logon section and locate theSecurity ID . This will show the user account that was affected by the logon.
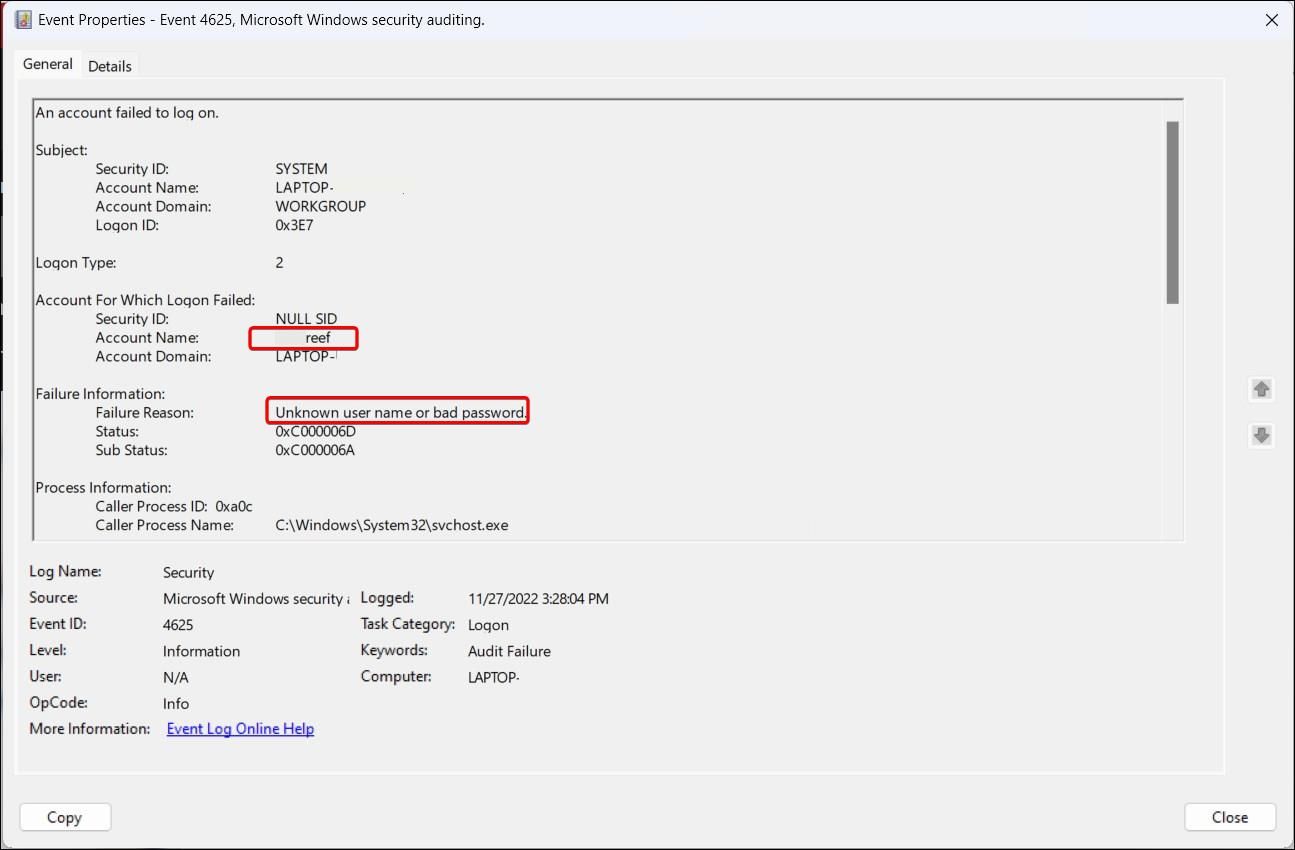
Similarly, for failed login attempts, reviewEvent ID 4625 . In theProperties dialog, you can find reasons for the failed login attempt and the affected user account. If you find multiple instances of unsuccessful attempts, consider learninghow to limit the number of failed login attempts to protect your Windows PC .
Below is the list of all nineLogon Types for logon events that you may encounter reviewing login events in Event Viewer:
| Logon Type | Description |
|---|---|
| Logon Type 2 | A local user logged on to this computer. |
| Logon Type 3 | A user logged on to this computer from the network. |
| Logon Type 4 | Batch logon type without user intervention – Scheduled Tasks, etc. |
| Logon Type 5 | Logon by system service started by Service Control Manager – Most common type |
| Logon Type 7 | System unlocked by a local account user |
| Logon Type 8 | NetworkClearText - Logon attempted over the network where the password was sent as clear text. |
| Logon Type 9 | NewCredentials – triggered when a user uses the RunAs command with the /netonly option to start a program. |
| Logon Type 10 | RemoteInteractive – Generated when a computer is accessed via a remote access tool such as Remote Desktop Connection. |
| Logon Type 11 | CachedInteractive – When the user logged on to the computer via console using the cached credentials when the domain controller is not available. |
How to View the Last Logon History Using Command Prompt
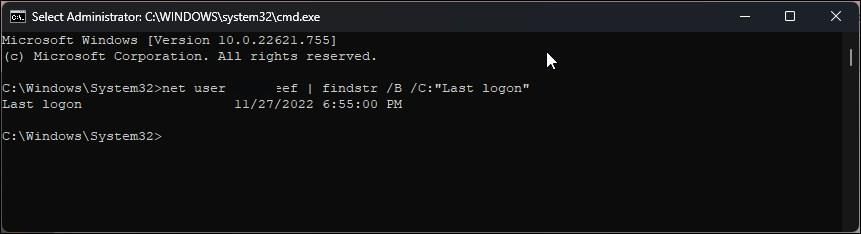
You can use the Command Prompt to view the last login attempt. It is a handy way to find user-based login attempts without having to go through all the logon events in Event Viewer.
To view the login history of a specific user using Command Prompt:
- PressWin + R to openRun .
- Typecmd . While holding theCtrl + Shift key , clickOK . This will open theCommand Prompt as administrator.
- In the Command Prompt window, type the following command and press Enter:
net user administrator | findstr /B /C:"Last logon" - In the above command, replace “administrator” with the username to view their login history.
- The output will show the last login time and date for the specified user.
Viewing Failed and Successful Login Attempts in Windows
If you suspect someone to have logged in to your PC, the Event Viewer will likely catch and record the attempt. For this to work, you must enable the Logon Auditing policy in Group Policy Editor. You can also use Command Prompt to view a specific user’s login history.
That said, anyone who knows their way around Event Viewer can easily clear the logs. So, if anything, beefing up your Windows computer security is the best way to prevent unauthorized access. You can begin by limiting the number of failed login attempts on your Windows PC.
Also read:
- [New] Economical Android Communication Tools, Best of 10
- [Updated] FB Audio Clip Converter Direct to MP3 Mode
- [Updated] Revenue Optimization Leveraging Your YouTube Mobile Audience
- Bringing Dimensions to Life The #1 List of PC's Top VR 360 Players for 2024
- Efficiency at Its Peak: Streamlined Grouped Software Installs with Winstall on Windows 11
- Effortless Solutions to Restore Your Overwatch Voice Chat
- El Camino Optimo a La Codificación MP4 en 2Er Milenio: Selección Y Uso Del Software Perfecto
- Enhancing Phone Integration: Strategies for Windows 11
- How Windows 11 Outperforms Apple's macOS
- Optimize File Safety: Win's Delete Settings Guide
- Top 5 Solutions: How to Stop Constant Wi-Fi Drops on Your iPhone
- Troubleshooting: 6 Steps for Reviving a Defective Network Card in Windows
- Title: Keep an Eye on Your Window's Gatekeeping Credentials Trend
- Author: David
- Created at : 2024-11-05 21:58:59
- Updated at : 2024-11-07 19:15:38
- Link: https://win11.techidaily.com/keep-an-eye-on-your-windows-gatekeeping-credentials-trend/
- License: This work is licensed under CC BY-NC-SA 4.0.