Detecting Hacker Activity on a Windows Device

Detecting Hacker Activity on a Windows Device
Keyloggers, cryptojackers, spyware, and rootkits are all types of malware that hackers use to infect victims’ devices. While some of these infections let hackers remotely connect to the victim’s computer, others monitor the person’s keystrokes, use the system’s resources, or simply spy on the targeted person’s activity.
If you suspect that your Windows device might have been hacked, here are some practical steps you can take to check that.
Disclaimer: This post includes affiliate links
If you click on a link and make a purchase, I may receive a commission at no extra cost to you.
Before We Get Started…
Before investigating whether your device has been compromised, close all third-party and Windows applications. This will reduce the entries Task Manager or otherany alternatives to the Task Manager you might be using and allow you to effectively identify suspicious connections established on your computer.
Afterward,run a malware scan on your device using Microsoft Defender or any reliable third-party antivirus software you usually use. This step will help you detect and automatically remove light infections inside your device, and they won’t distract you when searching for more severe infections or security breaches.
Once you have closed down all nonessential processes and carried out a malware scan, you can start looking for any malicious programs lurking on your system.
How to Inspect Your Device for Spyware or Hacking Attempts
In the modern era, malware infections are usually programmed to actively (but secretly) operate on the victim’s computer. For instance,cryptojackers use victims’ computer resources for crypto mining, keyloggers gather login credentials by monitoring keystrokes, and spyware tracks users’ activity in real-time and shares it with the hackers.
Each of these malware types relies on a remote connection to the hacker’s server where the data is sent, the mining software runs, or whatever else the hacker is trying to accomplish. By identifying those suspicious connections established on our device, we can determine whether our device has actually been compromised.
1. Check for Suspicious Connections
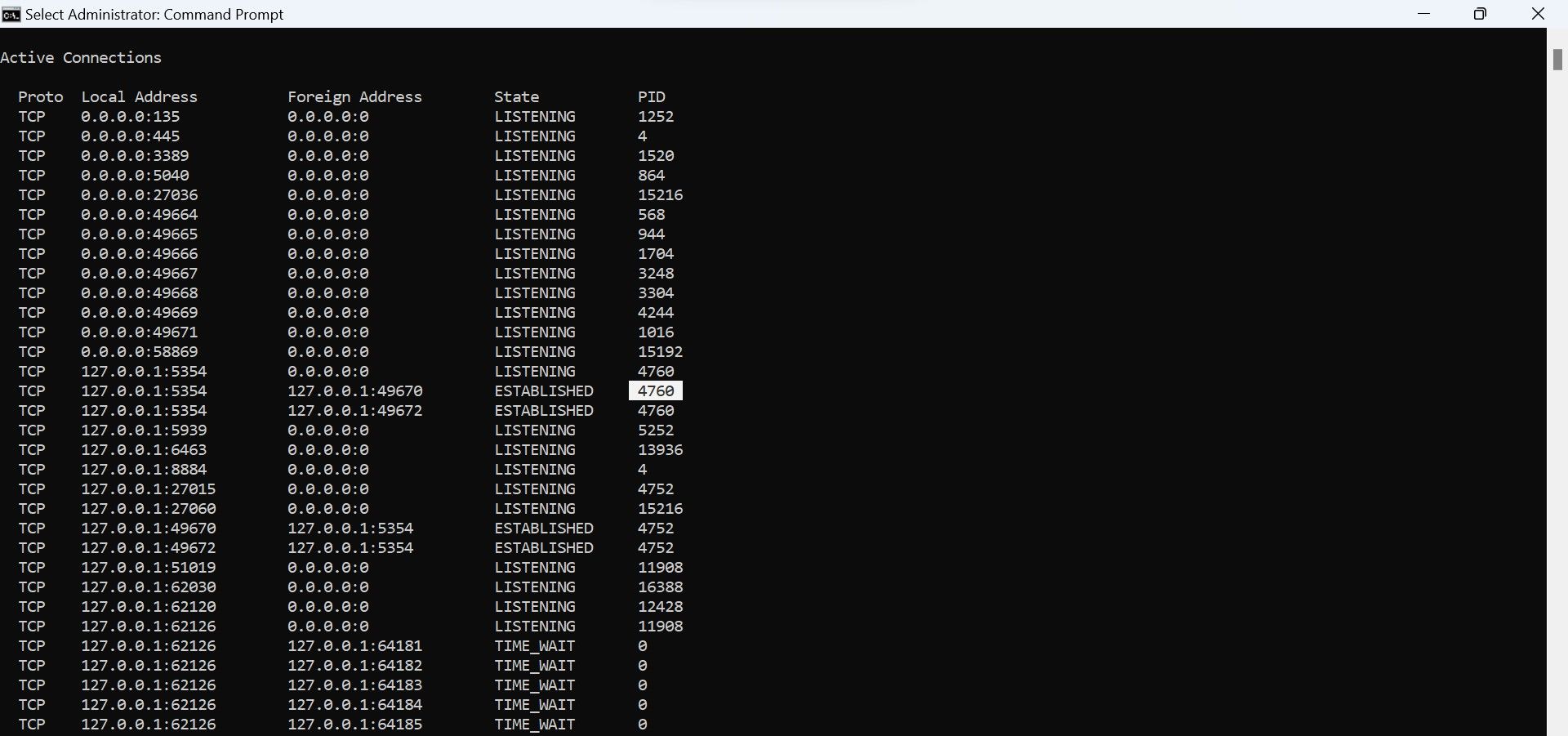
You can check for suspicious connections on your computer in several ways, but the method we’ll show you will use a built-in utility in Windows called the Command Prompt. Here’s how you can find the remote connections set up with your device using Command Prompt:
- Type**”Command Prompt”** in Windows Search.
- Right-click theCommand Prompt app and clickRun as administrator .
- Simply type the following command and hitEnter .
netstat -ano
The above command will show you all the TCP connections the apps, programs, and services have established to remote hosts.
Pay attention mainly to theState column, where you’ll find three main terms:Established ,Listening , andTime_Wait . From these three, focus on the connections whose state identifies asEstablished . The**”Established”** state indicates a real-time connection between your computer and the remote IP address.
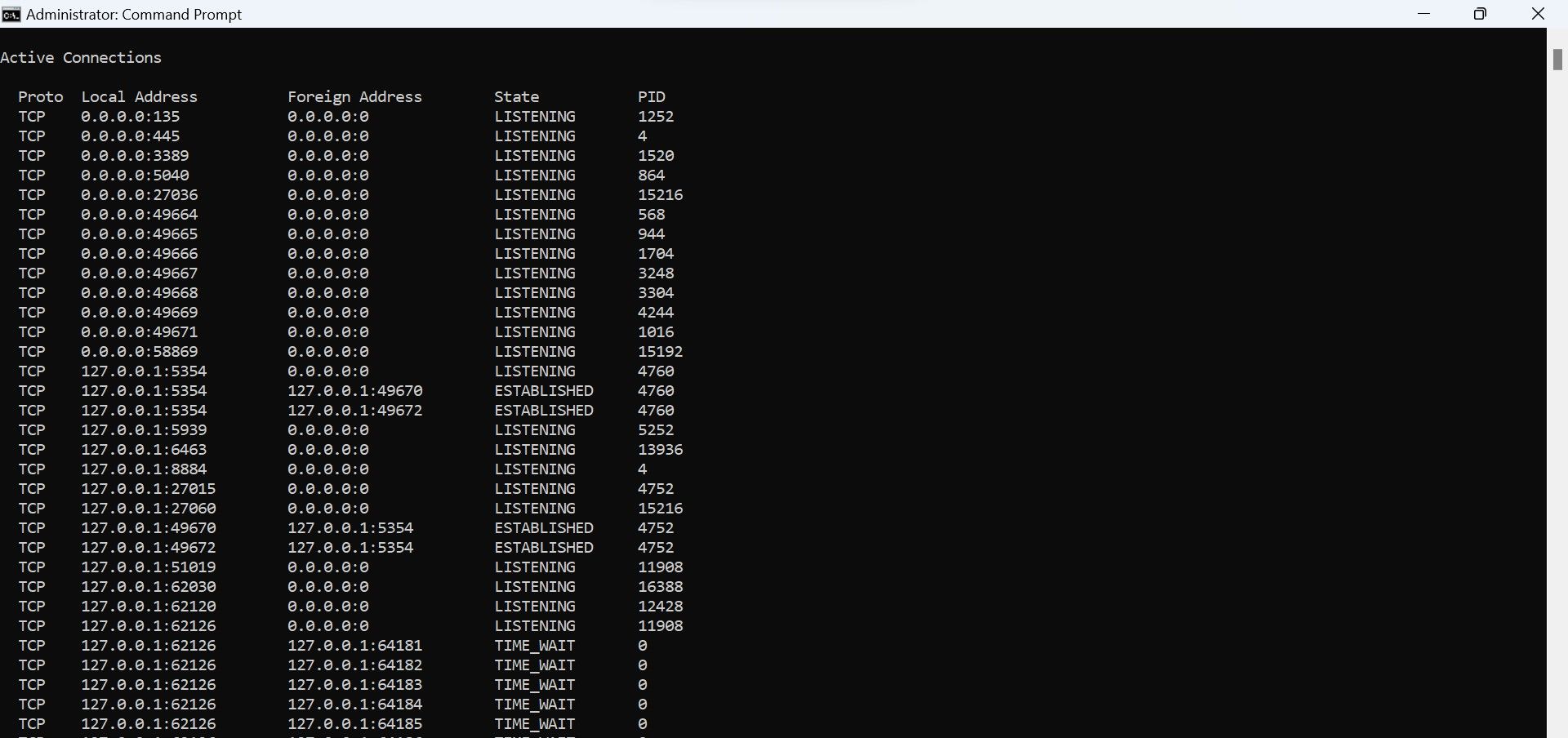
Don’t panic if you see a lot of established connections. Most of the time, these connections are made to a company server whose services you use, like Google, Microsoft, etc. However, you need to analyze each of these connections separately. This will help you determine if there are suspicious connections being made to a hacker’s server.
Do not close the Command Prompt; we will use the netstat information in the next steps.
2. Analyze Any Connections That Seem Suspicious
Here’s how you can analyze the suspicious connections:
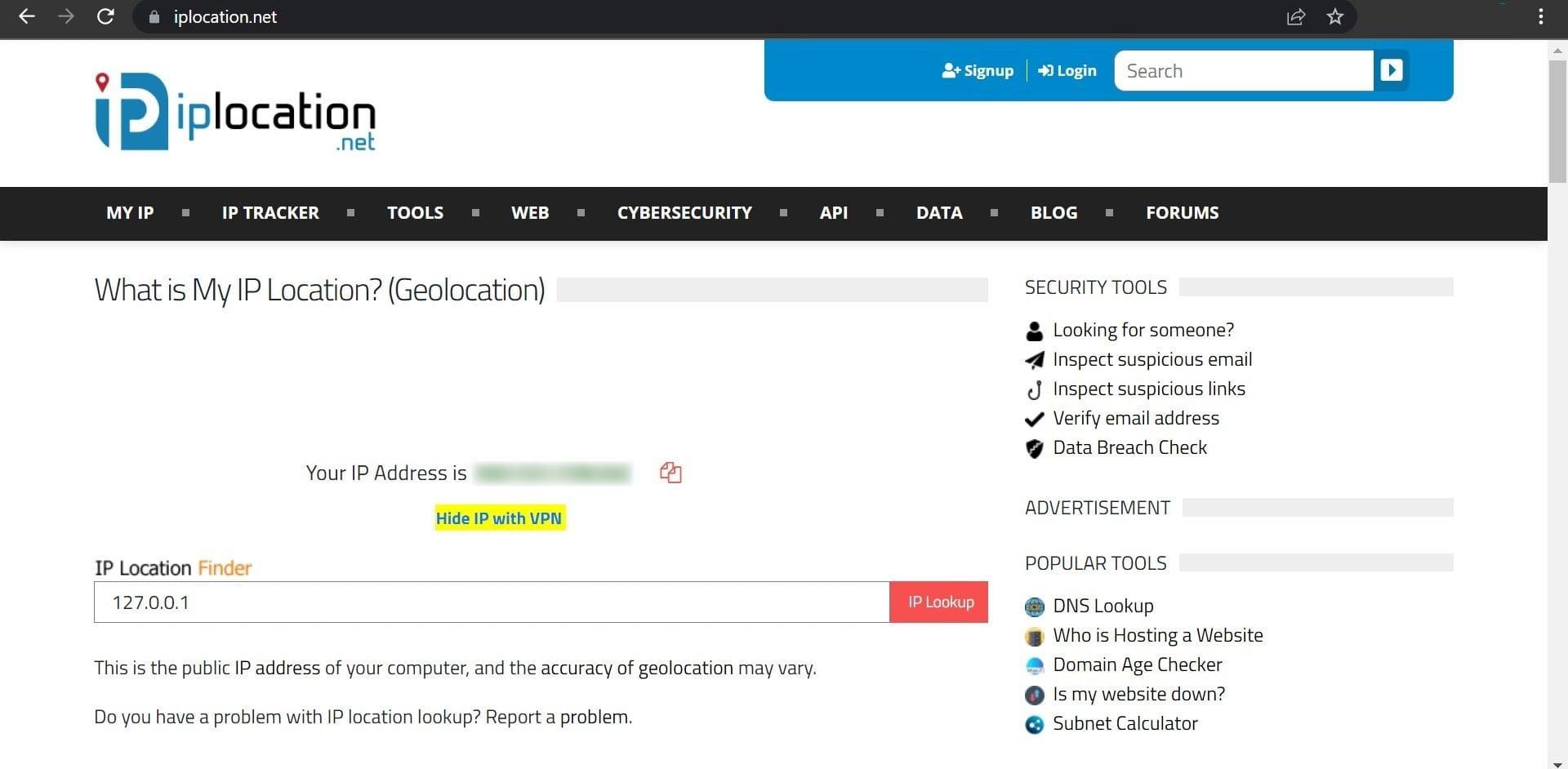
- Copy the IP address from theForeign Address column in theCommand Prompt .
- Go to a popular IP location lookup site, such as IPLocation.net.
- Paste your copied IP address here and click theIP Lookup button.

This website will provide you with information about the IP address. Check the ISP and organization that use this IP address. If the IP address belongs to a well-known company whose services you use, such as Google LLC, Microsoft Corporation, etc., there is nothing to worry about.
However, if you see a suspicious company listed here whose services you don’t use, there is a good chance that someone is spying on you. Thus, you will need to identify the process or service using this address for remote connection to ensure it isn’t malicious.
3. Find and Analyze Any Malicious Processes
To locate the malicious program scammers may have been using to snoop on your device, you have to identify the associated process. Here’s how to find it:
Note thePID next to the suspiciousEstablished connection in Command Prompt.

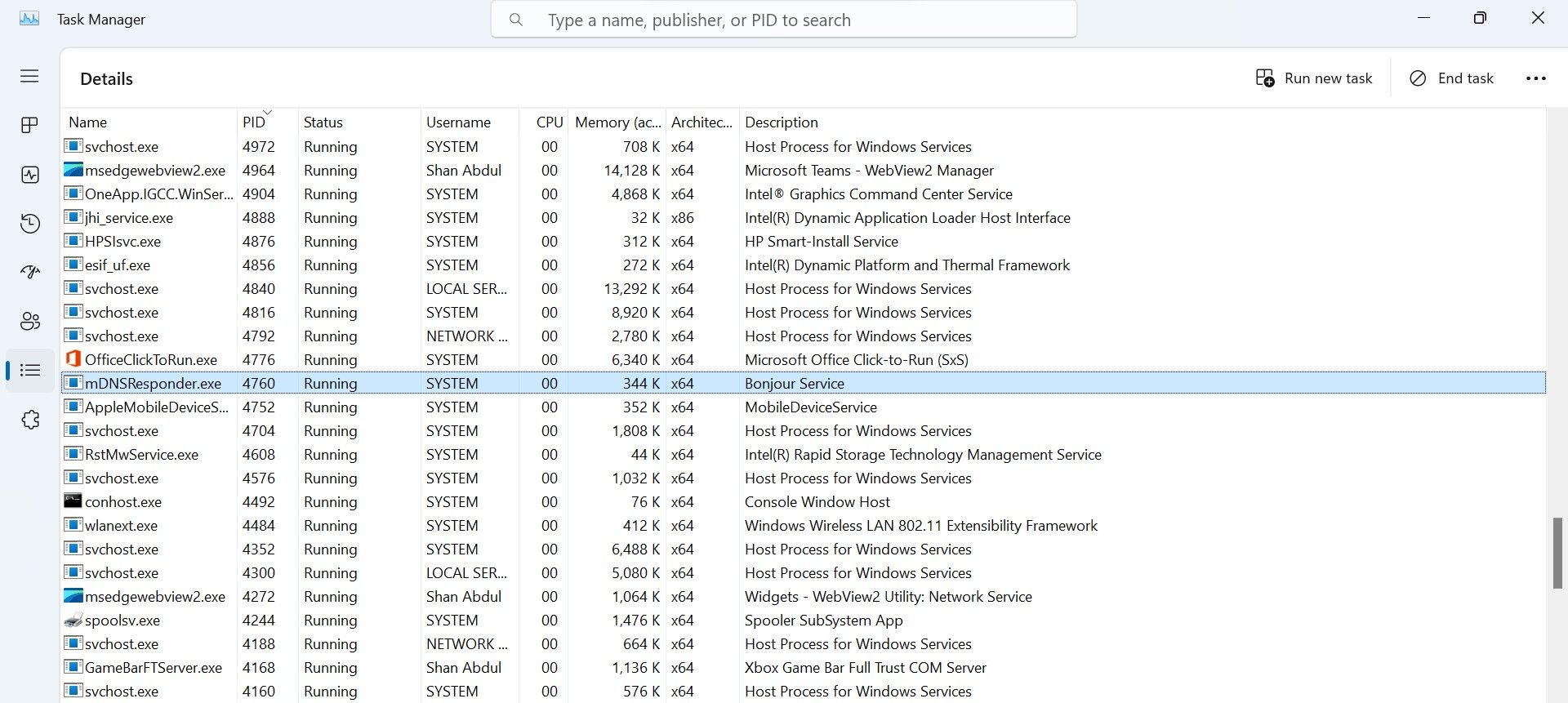
Open Task Manager. (See thedifferent ways to open Task Manager in Windows 10 and11 )
Go to theDetails tab.
Click thePID column to sort processes according to their PIDs.
Find the process with the samePID that you noted down earlier.

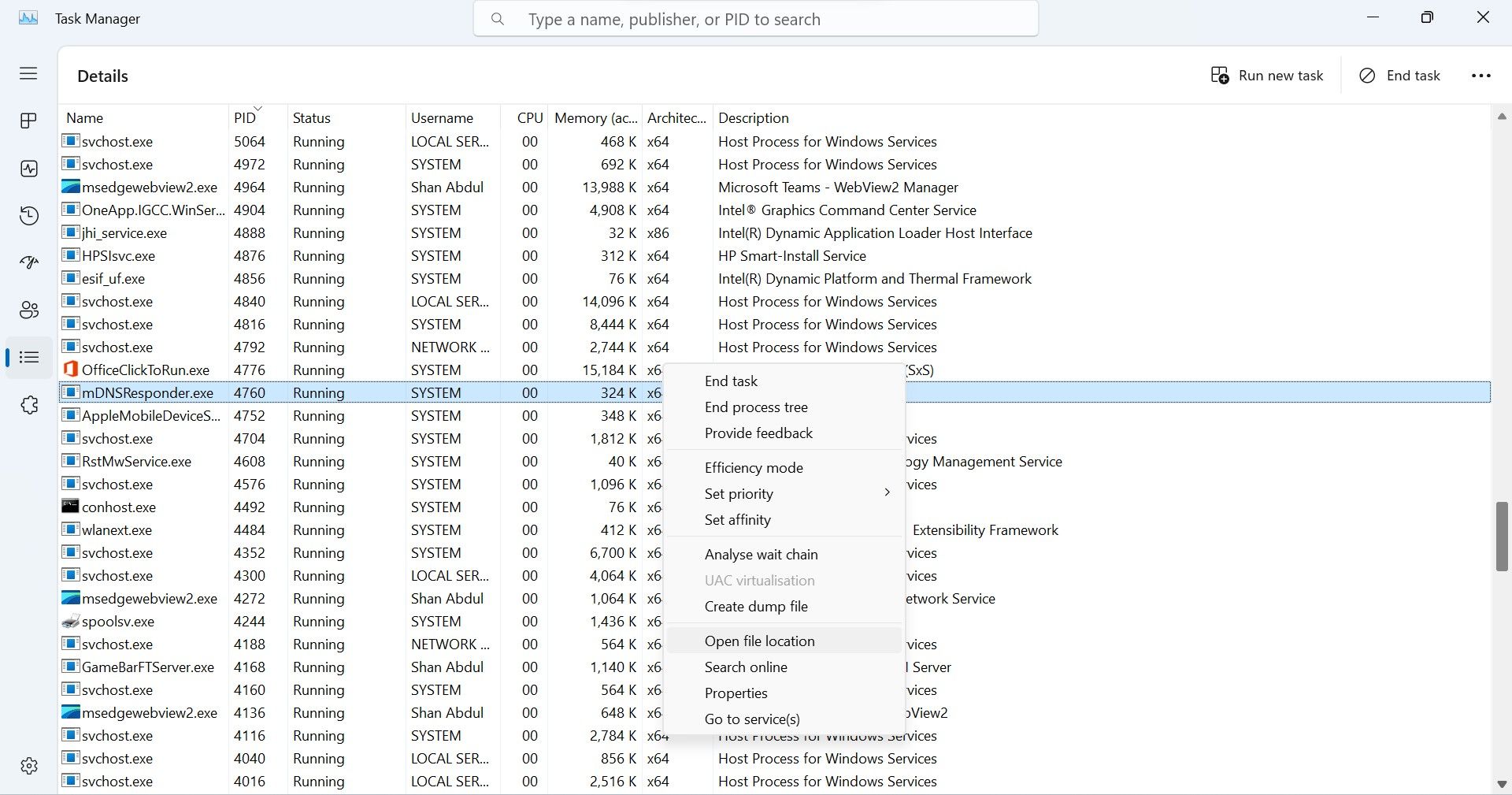
If the process belongs to a third-party service that you frequently use, you don’t need to close it. However, you should still verify that this process belongs to the company you believe it does,as a hacker can hide their malicious processes under the guise of a malicious one. So, right-click on the suspicious process and selectProperties .
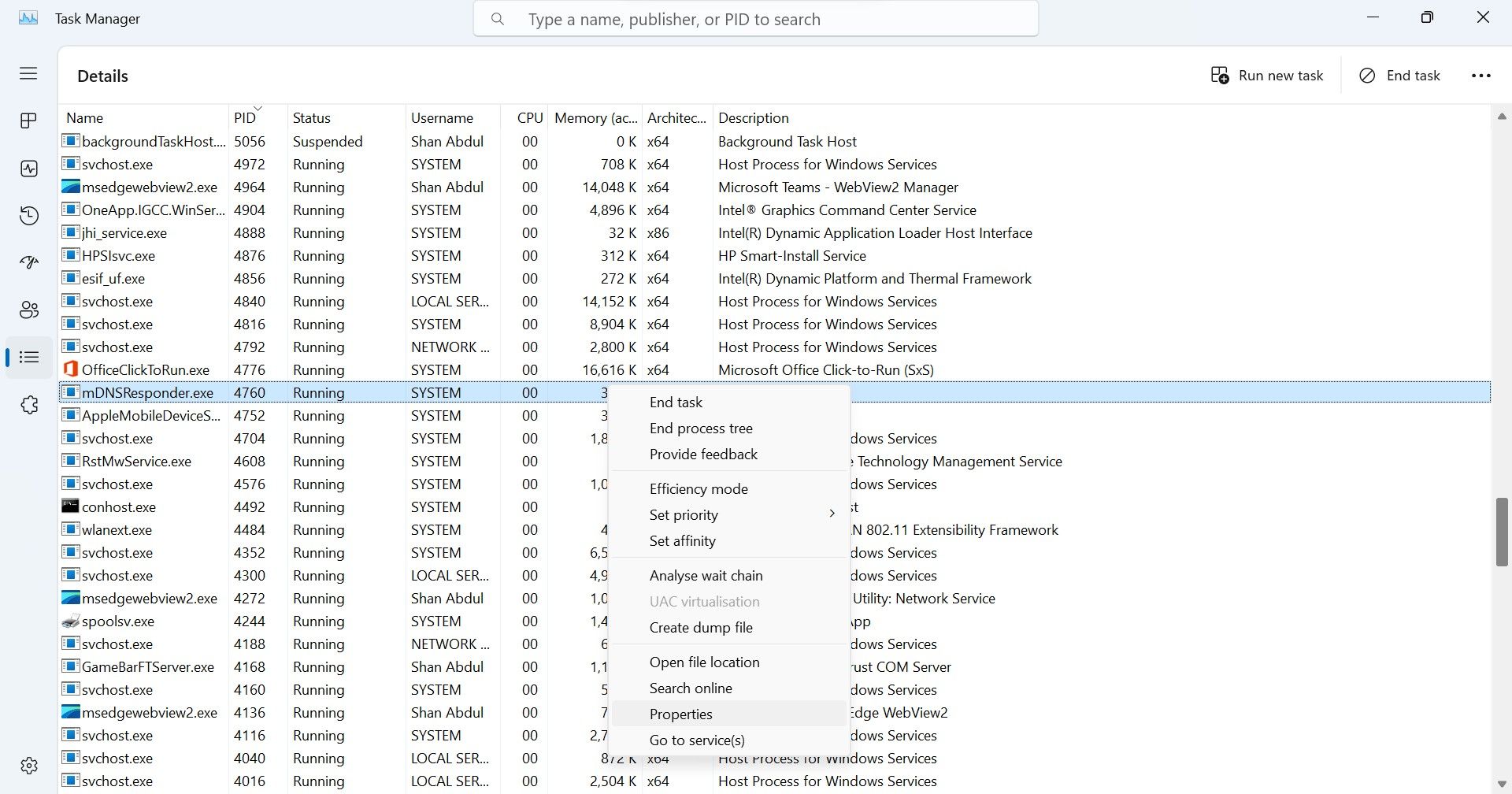
Then, navigate to theDetails tab for more information about the process.
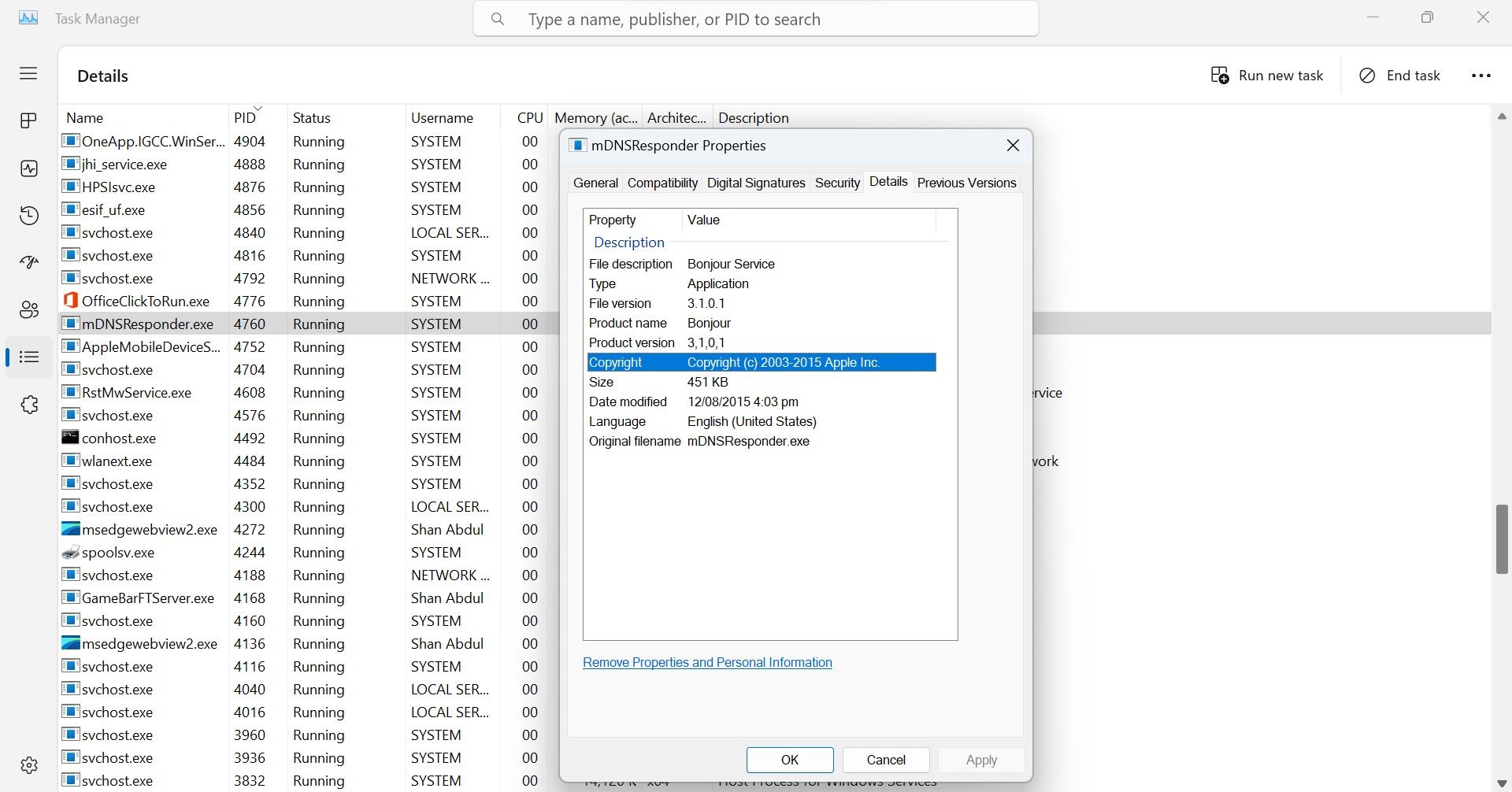
If there is any discrepancy in process details or the process itself seems suspicious, it is best to remove the associated program.
4. Remove Any Suspicious Programs
To identify and remove the malicious apps behind these suspicious processes, follow these steps:
Right-click the shady process and selectOpen file location .

Once again, ensure the file is not associated with Windows or any other critical application.
If you’re sure it’s malware, right-click it and delete it.

5. Take Professional Help When Necessary
Hopefully, following the above process will help you detect and remove the malicious program, thereby preventing hackers from spying on or stealing your personal information.
However, you should be aware that hackers can conceal their malware from netstat output by programming it that way. Likewise, they can code the program so it does not appear in Task Manager. Seeing no suspicious connections in the netstat output or not finding the suspicious process in Task Manager doesn’t mean your device is safe.
Therefore, if you see signs of a hacked device in your system, such as high resource consumption in Task Manager, system slowdowns, unknown apps getting installed, Windows Defender turning off frequently, the creation of suspicious new user accounts, and similar, you should consult a professional. Only then can you be sure that your device is completely secure.
Don’t Let Hackers Spy on You for Long
Microsoft consistently updates the Windows operating system to make it more secure, but hackers still find loopholes and hack into Windows devices. Hopefully, our guide will help you identify if any suspicious hacker is monitoring your activity. If you follow the tips correctly, you’ll be able to remove the suspicious app and disconnect the connection to the hacker’s server.
If you’re still suspicious and don’t want to risk your precious data, you should seek professional assistance.
Also read:
- [New] 2024 Approved Saving Instagram's Finest in Your Photo Gallery
- [New] Telltale Signs Your Chat Is Hidden
- [New] Top Tips to Nail Every Green Screen Scene
- [Updated] From Phone Ideas to Online Presence Simple YouTube Channel Creation Tips
- [Updated] Top 11 Pro-Level Screen Recorders for Mac Users
- 2024 Approved Expert Strategies for Clear Communication on Google Meet
- 2024 Approved Inside Look at Optimizing Channels in YouTube Studio
- 2024 Approved Next-Gen Recording Nine Leading Webmicrone Recorders ('23)
- Comprehensive Solutions for Blue Screen of Death Error 0xC000021A on Win 10/8 [Issue Resolved]
- Enhance Notepad in W11 with Digital Oracle
- Expert Guide: Efficiently Erasing Image Borderlines
- How to Quickly Address Stalled Torrents on PC
- How to Upgrade Apple iPhone 6 Plus to the Latest iOS/iPadOS Version? | Dr.fone
- Procedures for Pairing AirPods to Windows Computers
- Reverse the Endless Storage Drain on Windows PC
- Simplified Explanations for Using BlueScreenView Tech
- Win11: Quick Solutions for Failed Item Drops
- Windows-Compatible Hardware Test Suites
- Winning Against Fakeware in Windows Marketplace
- Title: Detecting Hacker Activity on a Windows Device
- Author: David
- Created at : 2024-11-12 03:07:33
- Updated at : 2024-11-18 02:22:13
- Link: https://win11.techidaily.com/detecting-hacker-activity-on-a-windows-device/
- License: This work is licensed under CC BY-NC-SA 4.0.